These instructions explain how to establish administrative accesses for a Windows Virtual Machine using Identity-Aware TCP forwarding. It’s important to do this if your VM lacks an external IP address and cannot connect to the web.
IAP TCP forwarding is a secure method for sending RDP, SSH and other types of traffic to virtual machines without the need for an unique IP address. It gives a user more power to decide which machines their server connects to and accepts connections from.
Step 1. To set up IAP TCP forwarding, your Windows VM needs to be operational and ready for use. Make sure its settings are configured correctly on Google Compute Engine.
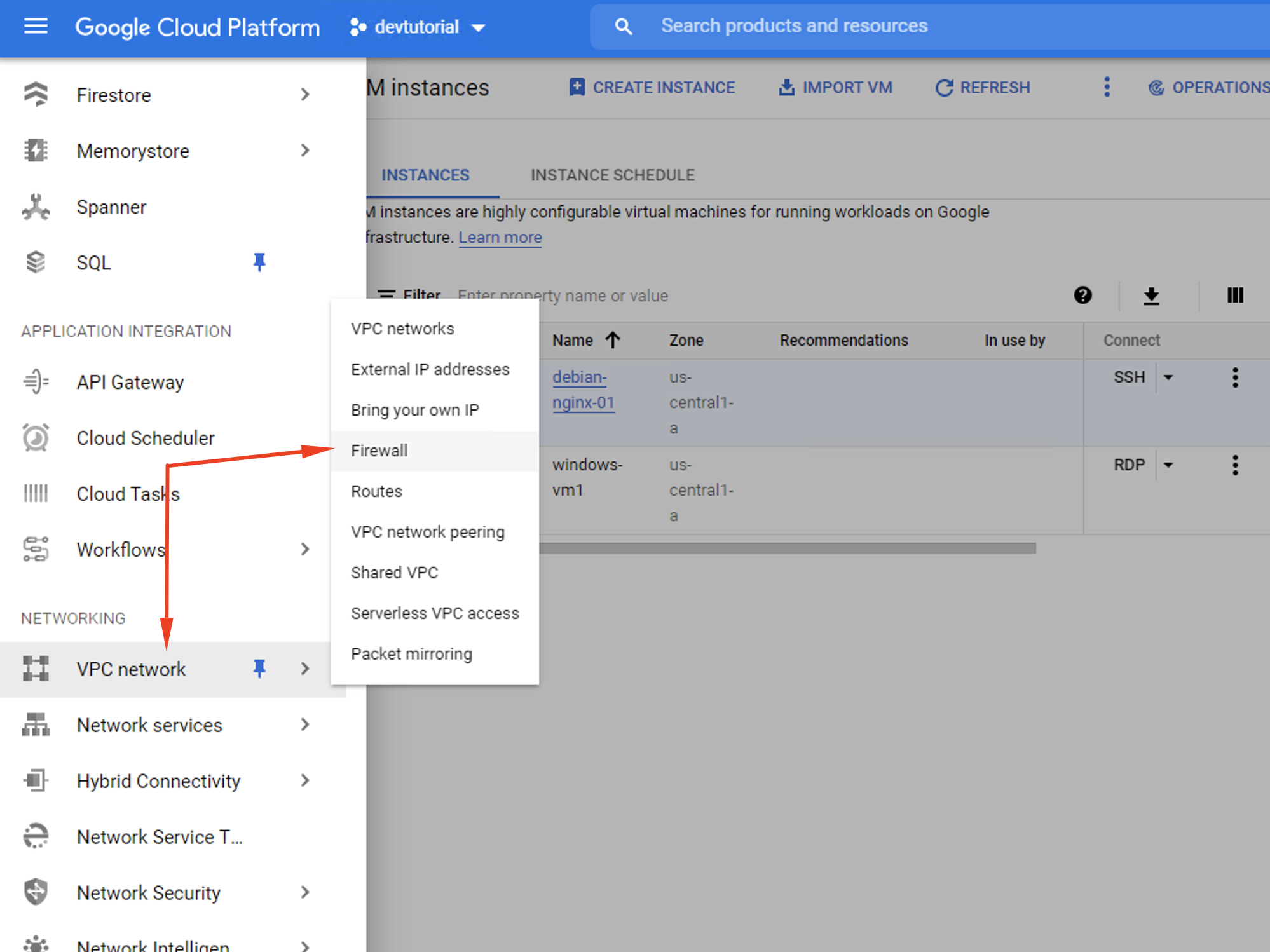
Step 2. Launch the Google Cloud Console. On the primary menu, click Networking, then VPC network.
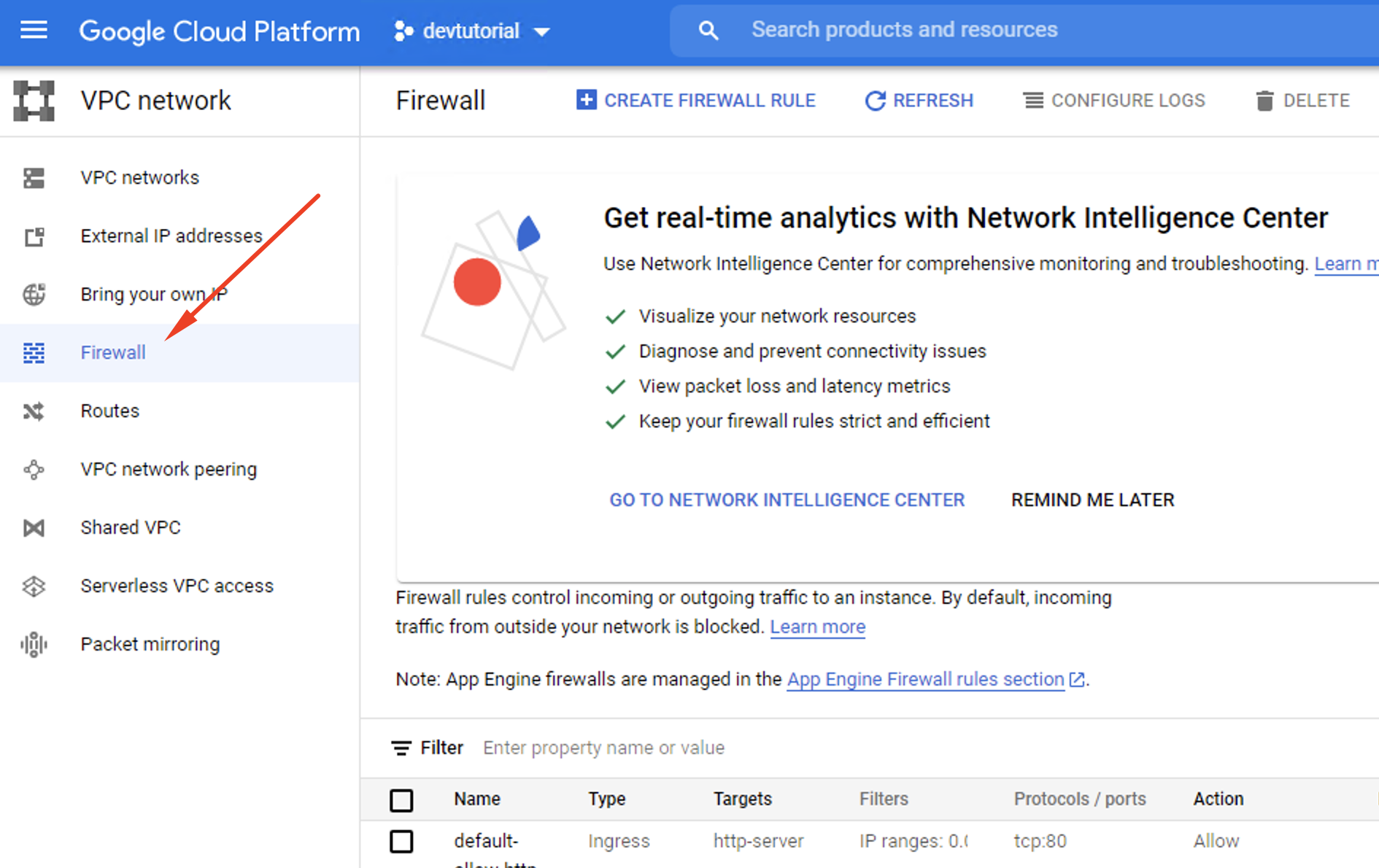
Step 3. Select Firewall on the next menu. Then, click Create a Firewall Rule.
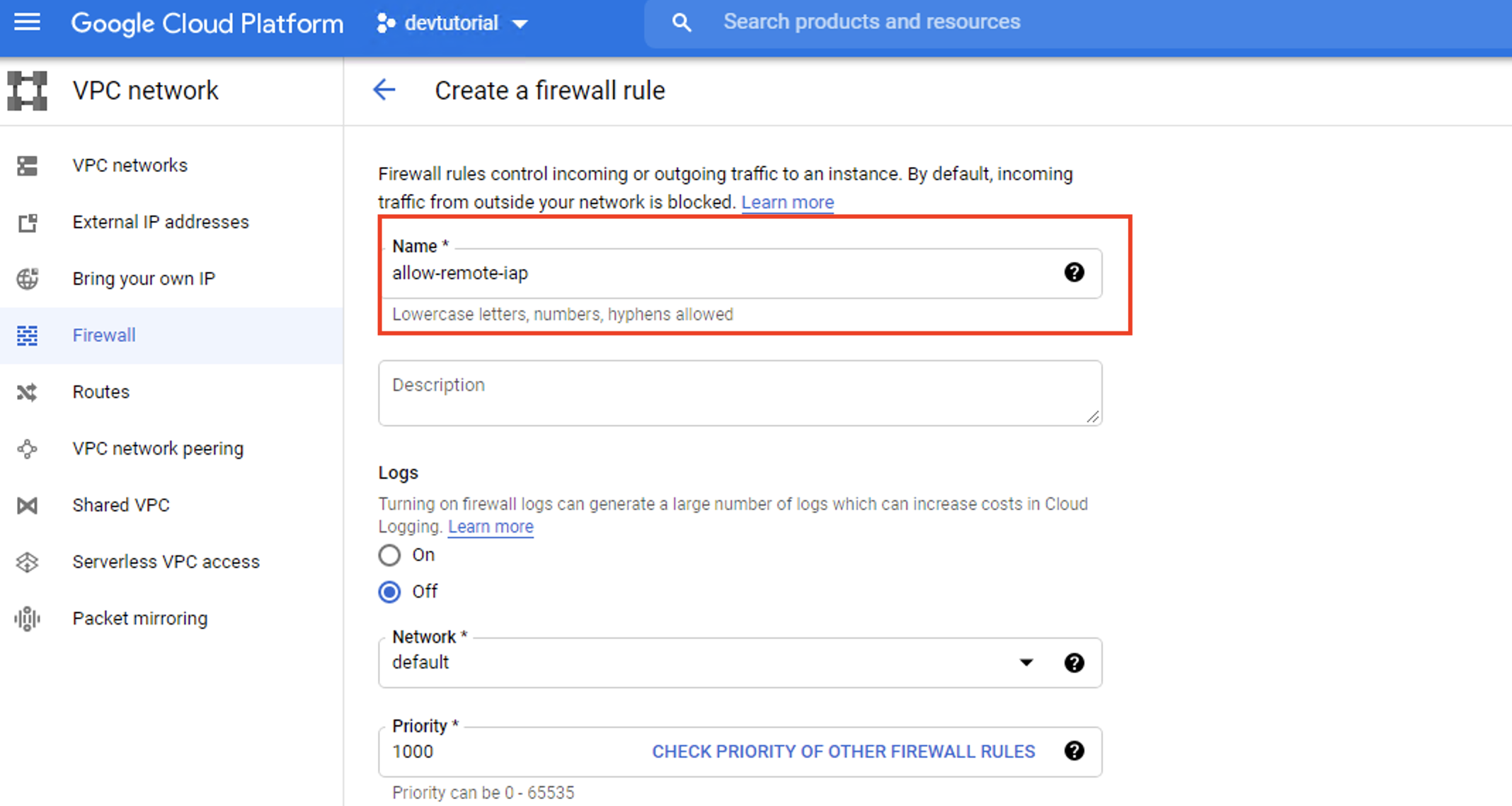
Step 4. Type the following into the box: allow-remote-iap.
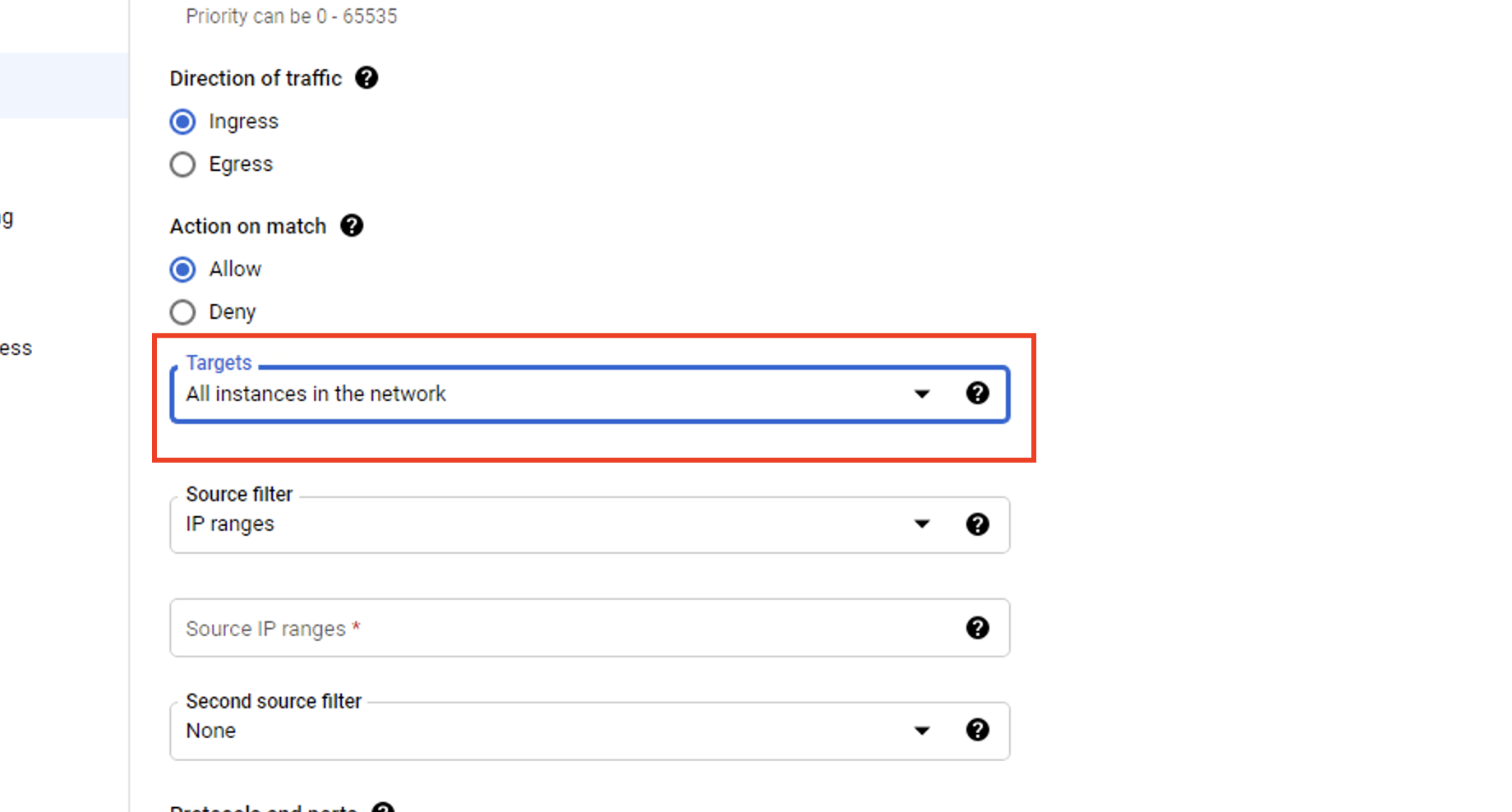
Step 5. Choose All instances in the network when asked to pick a target for the new firewall rule.
Step 6. Type the following into the box: 34.69.36.0/24 when asked to pick a source IP range for the new firewall rule.
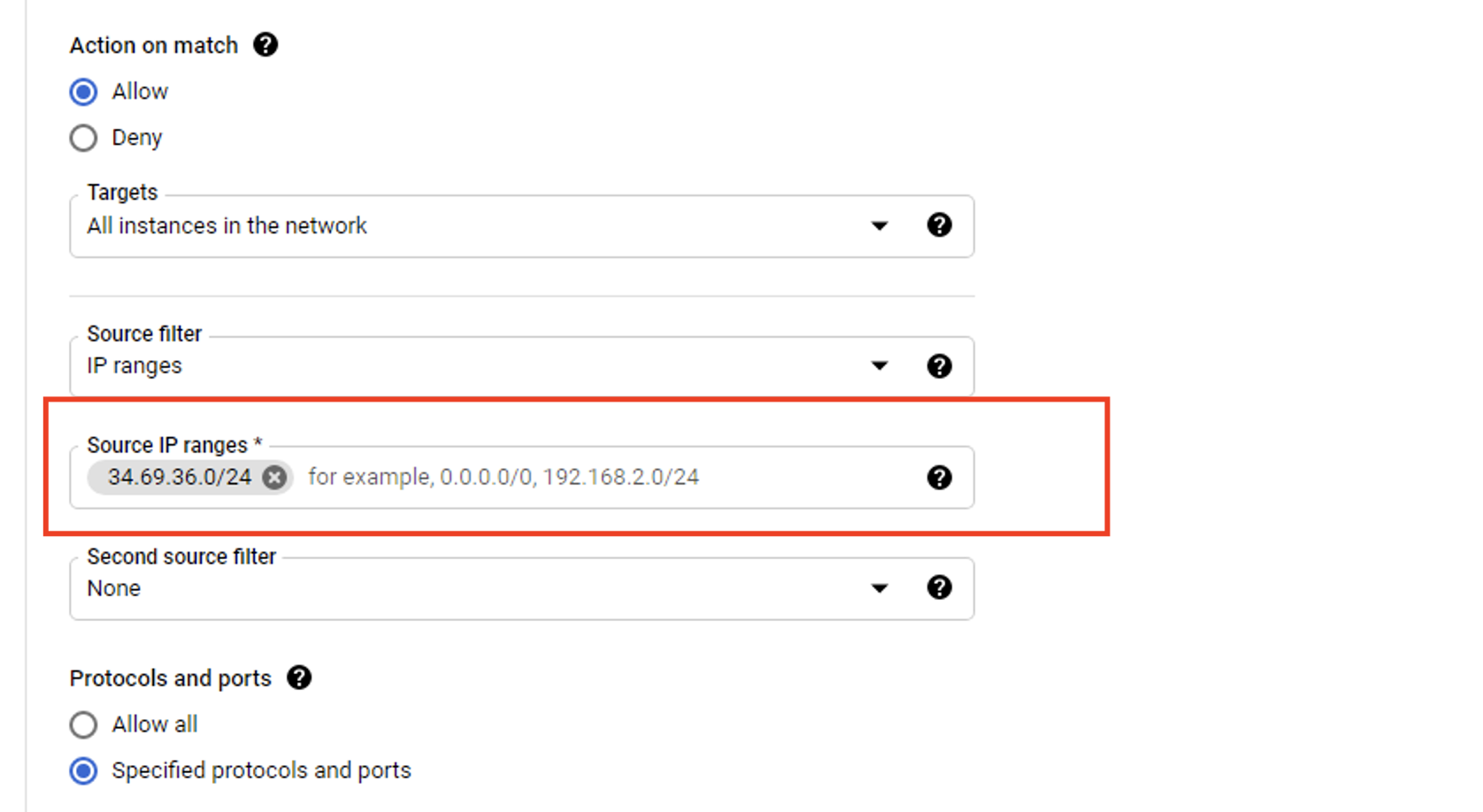

Step 7. In the Protocols and Ports menu, click TCP and type 3389 to enable RDP.
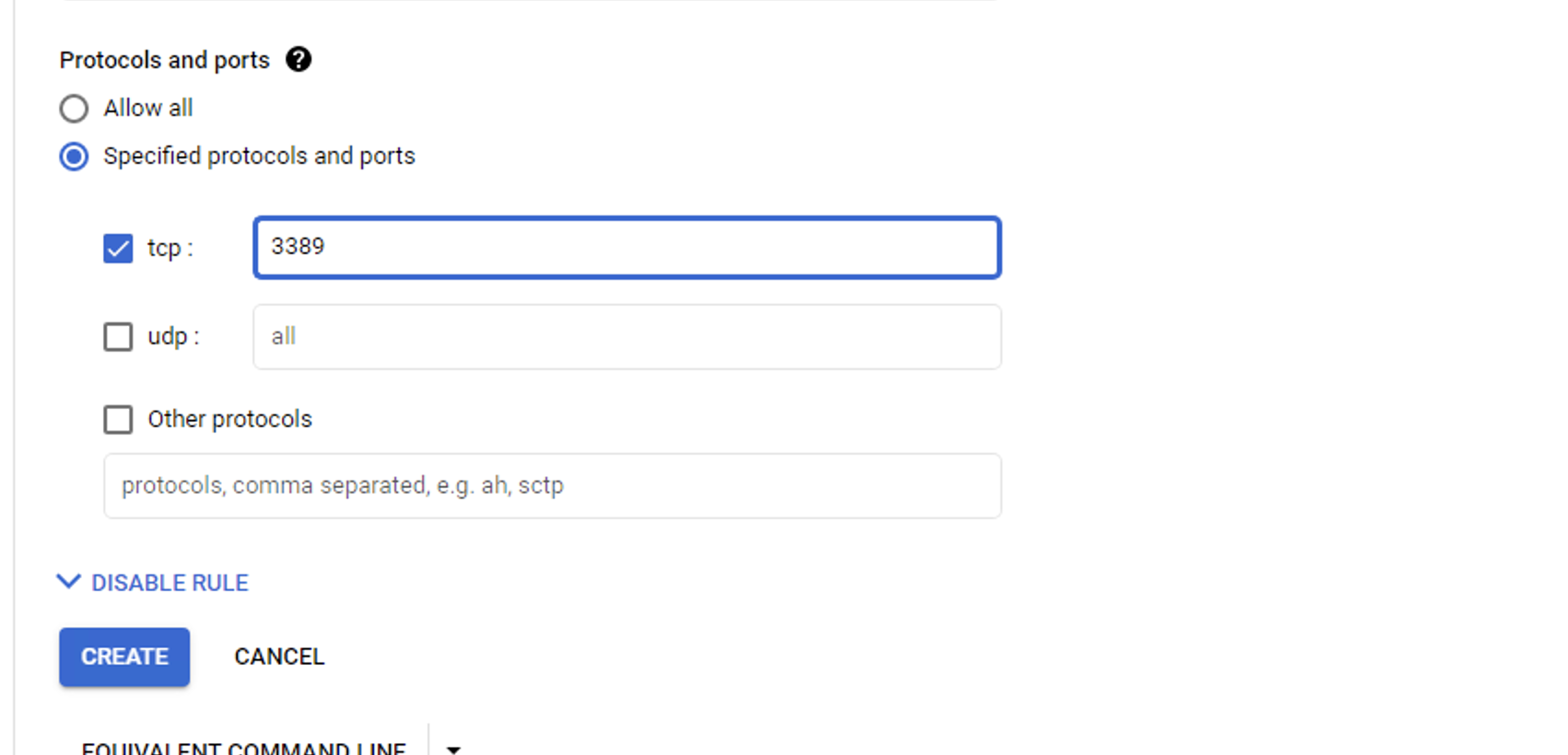
Step 8. Hit the Create button to save these new settings.
Step 9. Now, return to Google Cloud Console’s primary menu and select IAM & Admin.
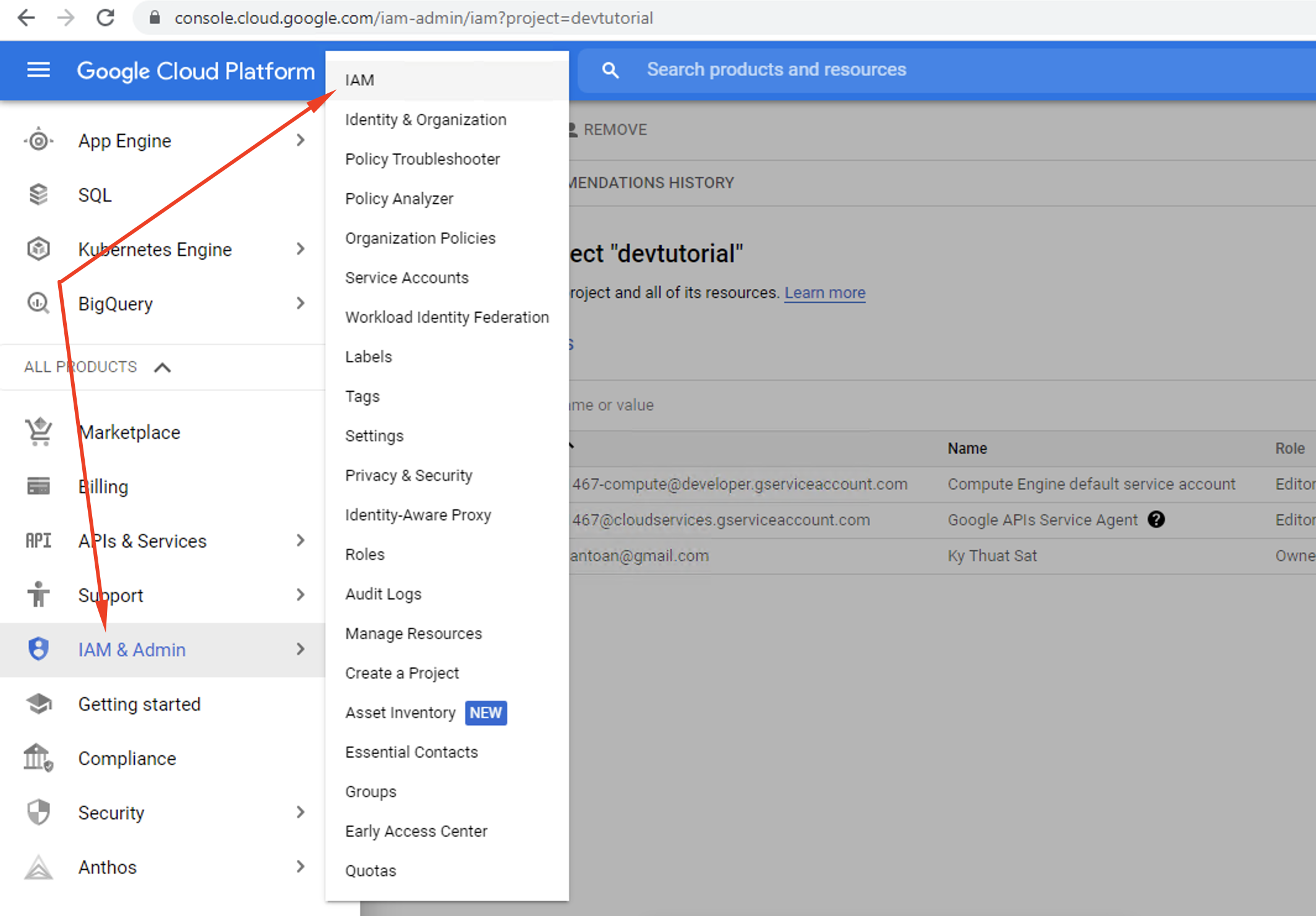
Step 10. Select Add new permission to set up new access rights to the IAP TCP forwarding for additional users. Users added to this list are allowed to connect to your Virtual Machines.
Step 11. For the members, select IAP-Secured Tunnel User as the designated role.
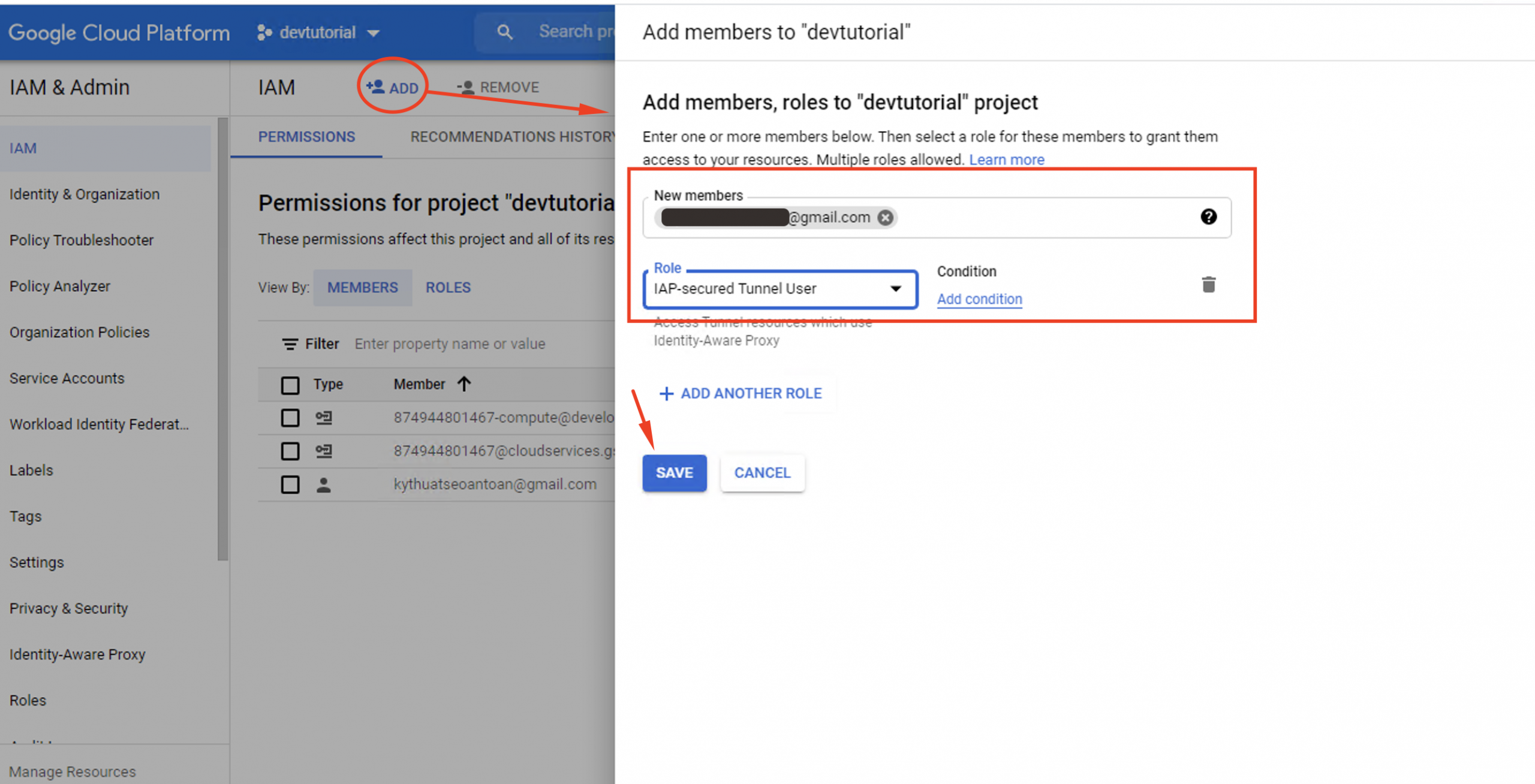
Step 12. Don’t forget to hit the Save button before you exit the menu.
Step 13. Finally, use the link below to install a secure version of IAP Desktop https://github.com/Google Cloud Platform/iap-desktop
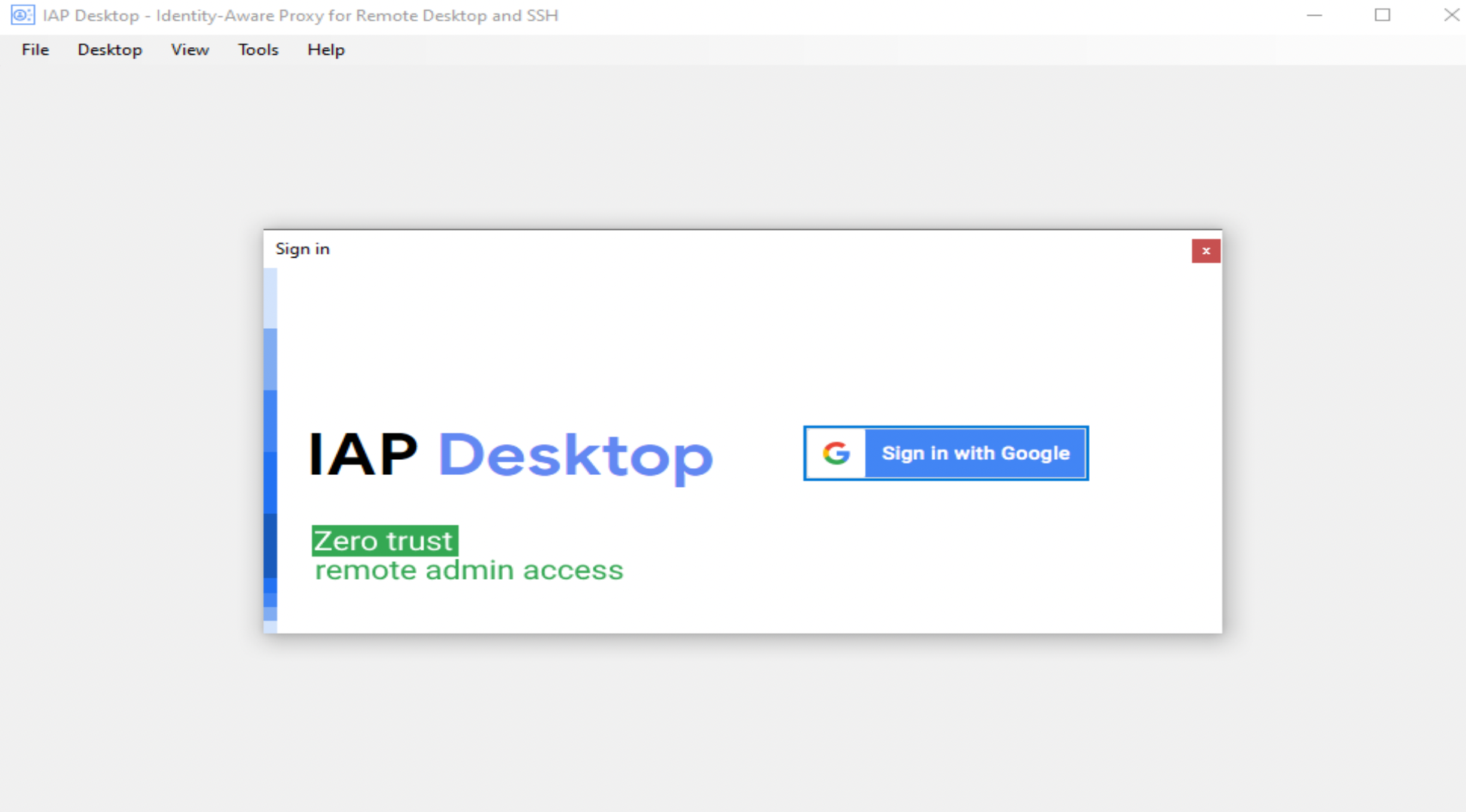
Step 14. Once downloaded, open IAP Desktop and log in with your user authorised account (see steps 10 and 11)
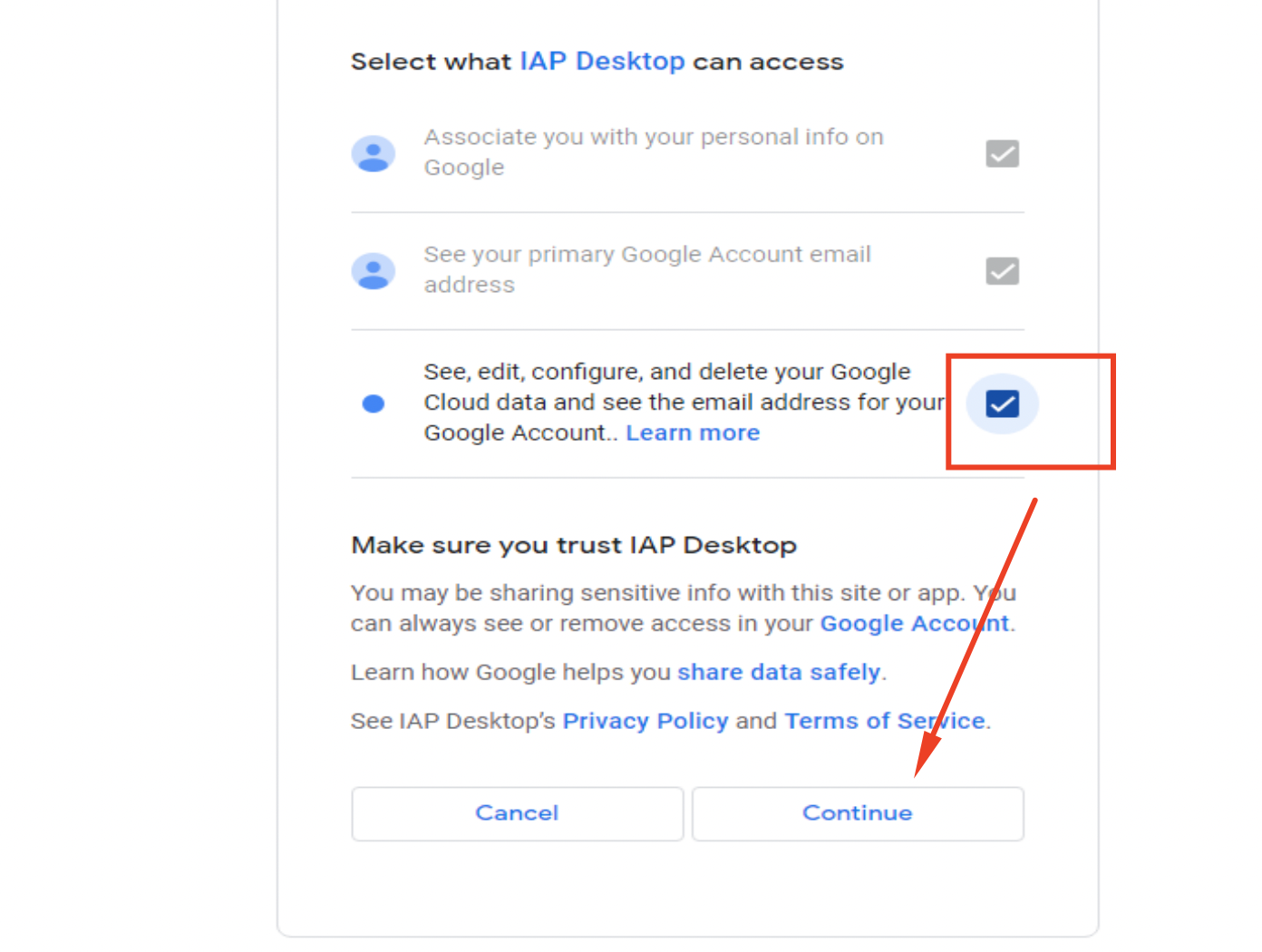
Step 15. Locate the relevant Google Cloud Project from the options presented.

Step 16. If your user account has been pre-authenticated, the name of your Windows VM should appear.
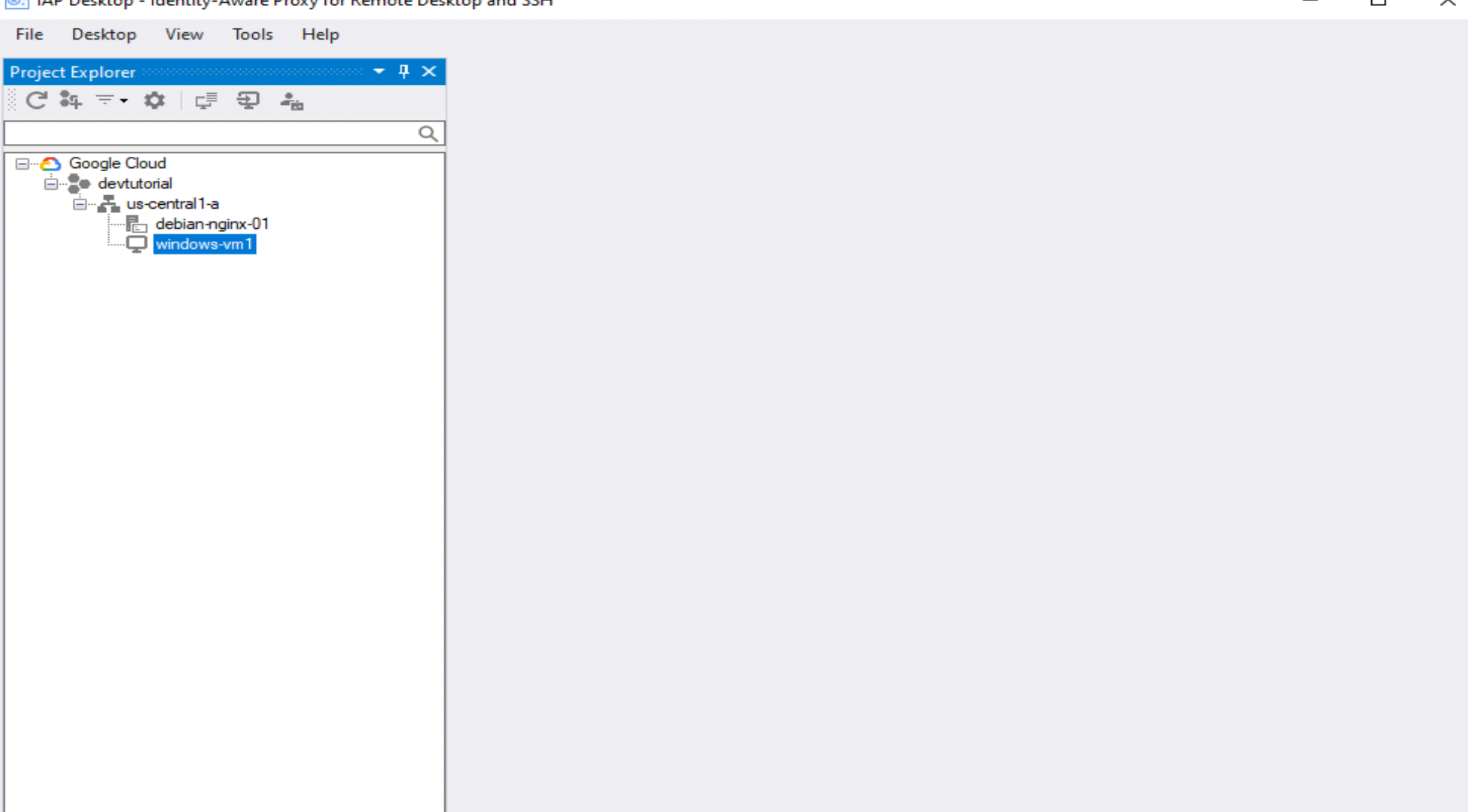
Step 17. Right click on the VM. Click Connect.
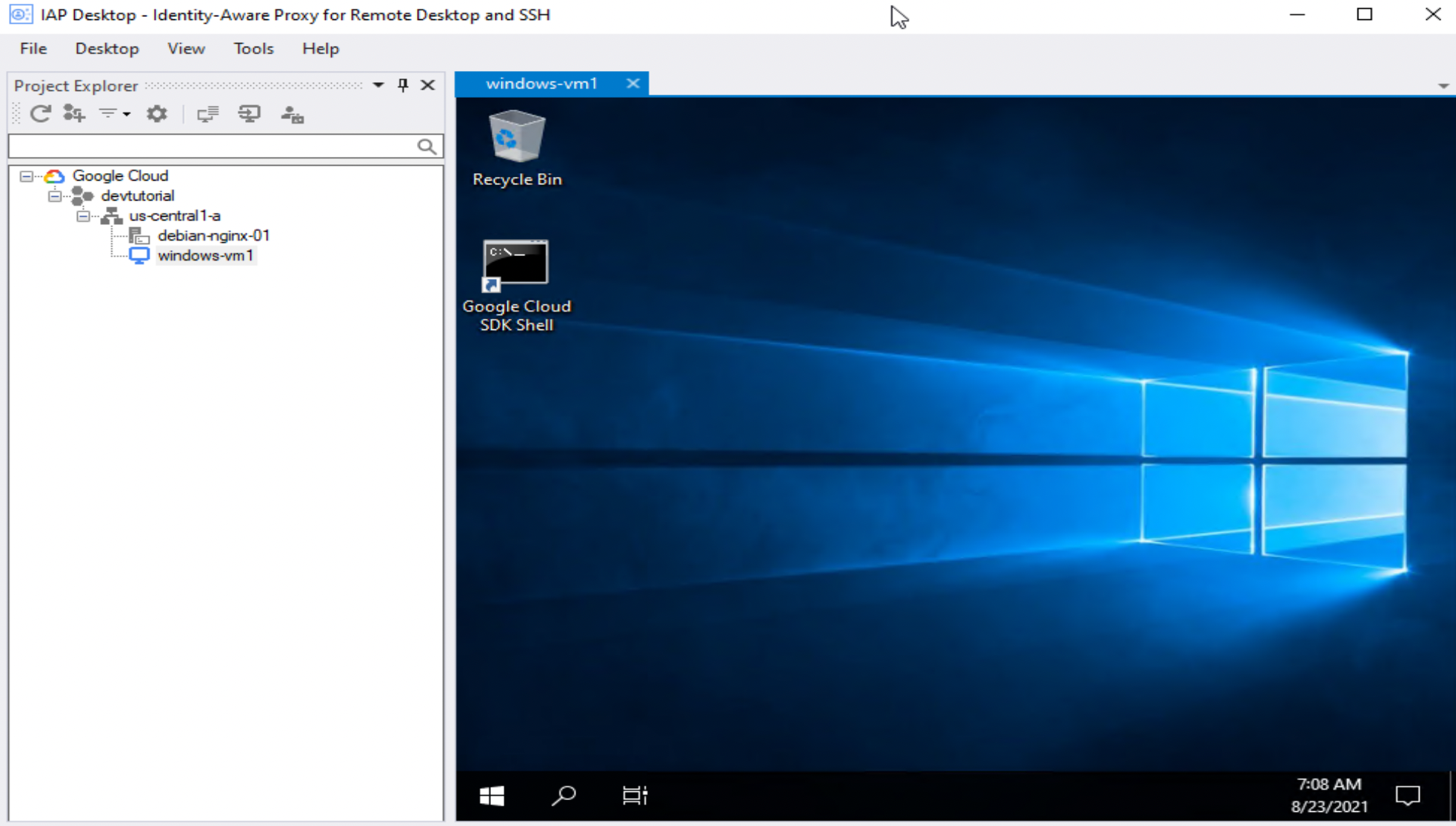
IAP TCP forwarding is a great way to establish a comprehensive permissions 'gate' for VM applications. Follow the steps outlined above to use an Identity-Aware Proxy for securely directing RDP traffic to and from a Windows VM.
If you use the IAP desktop client to authenticate your user connect on Google Cloud Compute engine, you shouldn’t have to repeat these steps again. Your user profile will be recognised as secure and permitted.